Delete bridge interface via Linux command
https://unix.stackexchange.com/questions/31763/bring-down-and-delete-bridge-interface-thats-up
Create Private Docker Registry for MiniKube
- Edit /etc/hosts and map host
<$minikube ip> host.minikube.internal Add insecere-registries=”host.minikube.internal:5000″ in daemon.jsonRestart dockerStart minikube insecure modeminikube start –insecure-registry=host.minikube.internal:5000 –insecure-registry=192.168.1.37- Setup selfcert http://www.selfsignedcertificate.com/ and save host.minikube.internal.cert and host.minikube.internal.key
- Copy selfcert to minikube node
scp -i $(minikube ssh-key) -pr selfcert/ docker@$(minikube ip):
6.1 minikube ssh
6.2 sudo cp -rvf selfcert /etc/docker/certs.d/host.minikube.internal:5000
6.3 cd /etc/docker/certs.d/host.minikube.internal:5000 ; sudo openssl s_client -showcerts -connect host.minikube.internal:5000 < /dev/null | sed -ne ‘/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p’ > ca.crt
6.4 exit from minikube - Create docker user and password
docker container run -i –rm –entrypoint htpasswd registry:2.6.2
-Bbn admin password >> ./selfcert/htpasswd - Copy cert to host
cp cert to /etc/docker/certs.d
sudo cp -rvf selfcert /etc/docker/certs.d/host.minikube.internal:5000 - Create ca.crt file
openssl s_client -showcerts -connect : host.minikube.internal:5000 < /dev/null | sed -ne ‘/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p’ > ca.crt - Run registry
docker container run -itd -p 5000:5000
–name registry
–restart=always
-v /home/warawich/Documents/registry/selfcert:/certs
-v /home/warawich/Documents/registry/selfcert:/auth
-e “REGISTRY_AUTH=htpasswd”
-e “REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm”
-e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd
-e REGISTRY_STORAGE_DELETE_ENABLED=true
-e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/host.minikube.internal.cert
-e REGISTRY_HTTP_TLS_KEY=/certs/host.minikube.internal.key
registry:2.6.2 - Testing login from Host
docker login host.minikube.internal:5000 - Testing login from minikube
minikube ssh – docker login host.minikube.internal:5000
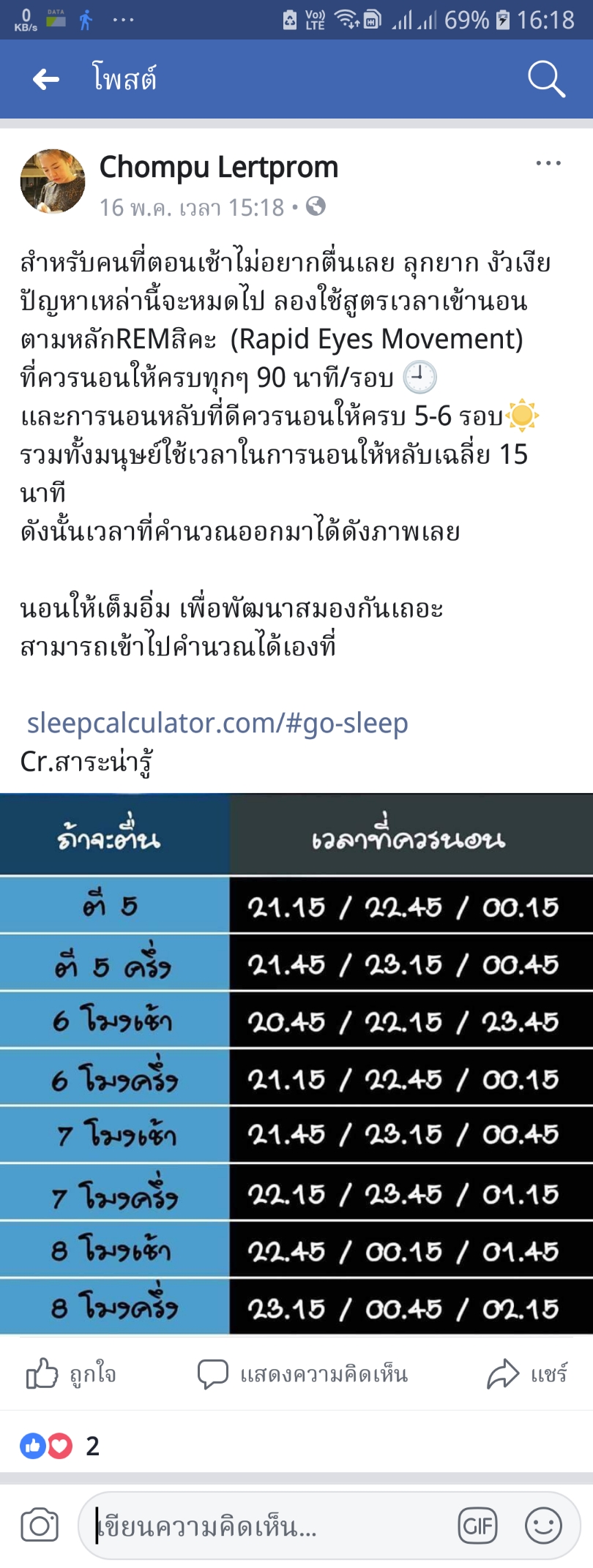
Time to sleep
Install PM2 Log rotate offline
1. Install pm2-logrotate from online computer with command
pm2 install pm2-logrotate
2. Compress file pm2-logrotate from pm2 module path
cd /root/.pm2/modules/ tar czvf pm2-logrotate.tgz pm2-logrotate/
3. Copy pm2-logrotate to offline computer
4. Decompress file to pm2 module path
cd /root/.pm2/modules/ tar xzvf pm2-logrotate.tgz
5. Start pm2 with command
pm2 start --name "pm2-logrotate" /root/.pm2/modules/pm2-logrotate/node_modules/pm2-logrotate/app.js pm2 save
If you want to change schedule, you can configure from file
vim /root/.pm2/modules/pm2-logrotate/node_modules/pm2-logrotate/package.json "config": {
"max_size": "10M",
"retain": "90",
"compress": false,
"dateFormat": "YYYY-MM-DD_HH-mm-ss",
"workerInterval": "30",
"rotateInterval": "0 0 * * *",
"rotateModule": true
},
Dockerize nginx with ssl letsencryt and with normal SSL cert
https://medium.com/@pentacent/nginx-and-lets-encrypt-with-docker-in-less-than-5-minutes-b4b8a60d3a71
1. edit file init-letsencrypt.sh
2. run ./init-letsencrypt.sh
3. docker-compose up -d
Generate token for Gmail account token access Node
Install Python multi version with pyenv
MongoDB เพิ่ม auth กรณีต้องการความปลอดภัย
1. Connect DB แล้ว run command ตามโน้น
use admin
db.createUser(
{
user: "myUserAdmin",
pwd: passwordPrompt(), // or cleartext password
roles: [ { role: "userAdminAnyDatabase", db: "admin" }, "readWriteAnyDatabase" ]
}
)
2. Shutdown Mongo
db.adminCommand( { shutdown: 1 } )3. Add config mongod.conf ตามนี้
security:
authorization: enabled4. Start mongo
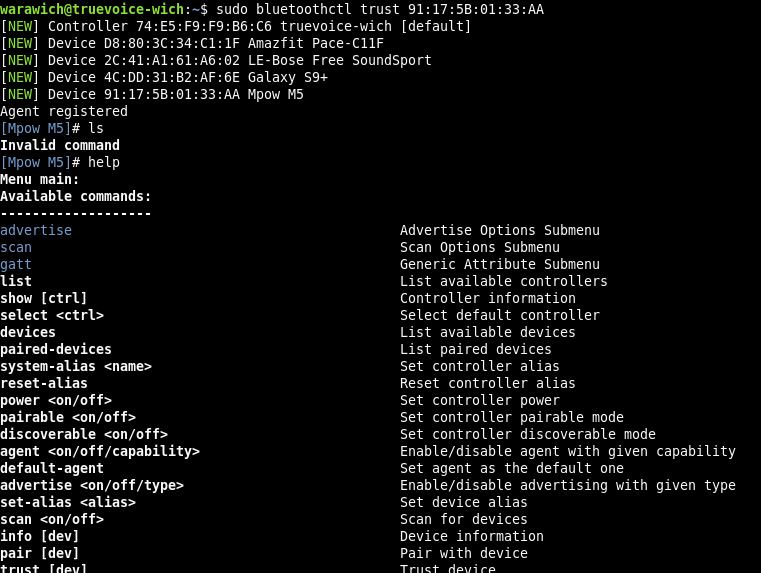
Trouble Shooting Bluetooth not automatic connect in Ubuntu
Ref: https://techwiser.com/fix-bluetooth-device-doesnt-auto-connect-in-linux/
[Mpow M5]# info 91:17:5B:01:33:AA